Last week, cybersecurity firm Mandiant published the details of a disruptive cyberattack in which the Russia-sponsored hacker group, Sandworm, targeted the critical infrastructure of a Ukrainian utilities organization. This incident was a multi-event cyberattack that leveraged a novel technique for taking down industrial control systems (ICS) and operational technology (OT) applications. The attack caused a major power outage.
Sandworm used hard-to-detect “living-off-the-land” (LotL) techniques to target OT applications, tripping the utility organization’s substation circuit breakers. This caused an unplanned power outage on critical infrastructure across Ukraine. The group later conducted a second disruptive event by deploying a new variant of the CaddyWiper malware in the target’s IT environment.
This attack is significant because existing network-based passive protections were ineffective in stopping this type of application level-based attack. A new approach is clearly needed to stop such attacks before harm is done to critical systems.
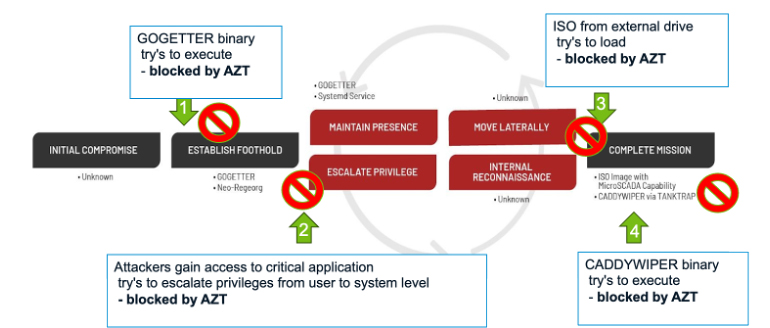
The graphic below shows Mandiant’s analysis of the attack – noting that the progression moves from left to right over time. Overlaid upon it we show where ARIA’s AZT PROTECT™ lightweight agent would have stopped the attack early as well as over its lifecycle. It demonstrates how the solution would be effective in transparently stopping the attackers from executing the attack before harm was done to the organization’s critical infrastructure applications.
Sandworm Attack – How ARIA AZT would stop it from doing harm
- Multiphase LotL attack – illustration where ARIA AZT PROTECT™ would intercept and stop the progression at each phase of the attack – out of the box
ARIA AZT PROTECT uses a patented approach to lock down critical applications from exploit, while blocking the execution of zero-day malware, and automatically stops the sophisticated techniques used by the most advanced nation-state sponsored attackers. It also deploys in minutes and instantly provides full protection, requiring no configuration to stop these attacks. It works in true air-gapped infrastructures and deploys on legacy, out-of-support OS-based critical devices in addition to today’s latest systems. Its ability to utilize less than 2% of a single core of CPU and less than 100 MB of device memory ensures it never disrupts or adds latency to the critical applications it protects. Furthermore, it deploys without requiring any reboots of the protected device OS or the hosted applications.
This attack represents the latest evolution in Russia’s cyberattack capability, which has been increasingly visible since Russia’s invasion of Ukraine. The techniques leveraged during the incident suggest a growing maturity of Russia’s offensive OT arsenal, including an ability to take advantage of vulnerabilities in critical OT vendor applications and the systems on which they run to execute the attacks. By using LotL techniques, the actor decreased the time and resources required to conduct its effective cyberattack to as little as two months. This indicates the capability of quickly developing similar capabilities against other OT systems applications from different original equipment manufacturers (OEMs) leveraged in utilities and energy companies across the world.
Background:
Sandworm is a full-spectrum threat actor that has carried out espionage, influence and attack operations in support of Russia’s Main Intelligence Directorate (GRU) since at least 2009. Beyond Ukraine, the group continues to sustain espionage operations that are global in scope and illustrative of the Russian military’s far-reaching ambitions and interests in other regions. Government indictments have linked the group to the Main Center for Special Technologies (also known as GTsST and Military Unit 74455).
Action:
Given Sandworm’s global threat activity and novel OT attack capabilities, we urge utility OT asset owners to act to mitigate this threat in the manner outlined above. Countries that have been high-profile in supporting Ukraine in their efforts to repel the Russian invasion – such as the US and in Europe – are particularly at risk.
If you need support building-out a simple to implement active defense, please contact CSPi Technology Solutions here.
Click for more information on AZT PROTECT
The blog post was originally posted on the Aria Cybersecurity Solutions website.